Creating and Using SSH Keys with DigitalOcean
About SSH Keys
SSH keys provide a more secure way of logging into a virtual private server with SSH than using a password alone. While a password can eventually be cracked with a brute force attack, SSH keys are nearly impossible to decipher by brute force alone.
Generating a key pair provides two long strings of characters:
- Public Key: Placed on the server.
- Private Key: Stored securely on your client machine.
When the keys match, the system unlocks without a password. You can further secure the private key with a passphrase.
On Mac or Linux
Step 1: Create the RSA Key Pair
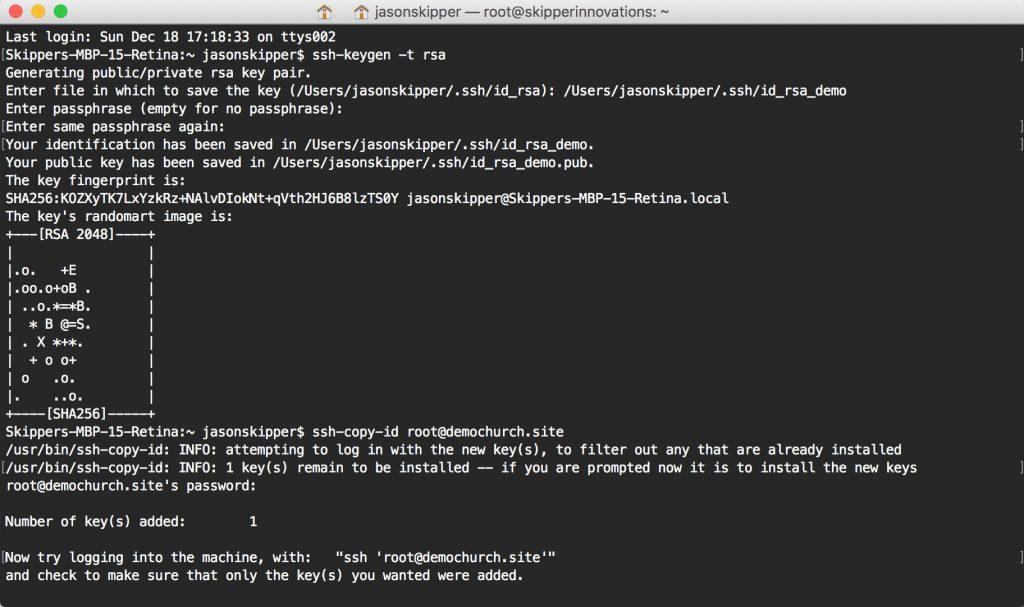
Run the following command to create the key pair:
ssh-keygen -t rsaStep 2: Store the Keys and Passphrase
Follow the prompts:
Enter file in which to save the key (/home/USER/.ssh/id_rsa):Press Enter to save the key in the default location.
Enter passphrase (empty for no passphrase):You can leave this blank or enter a passphrase for added security.
- Public Key:
/home/user/.ssh/id_rsa.pub - Private Key:
/home/user/.ssh/id_rsa
Step 3: Copy the Public Key to Your Server
Use the ssh-copy-id command to copy the public key to your server:
ssh-copy-id root@example.comAfter entering your server password, your public key will be added to the authorized_keys file.
You can now log into your server without being prompted for a password:
ssh root@example.comIf you set a passphrase, you’ll need to enter it when logging in.
On Windows with PuTTY
For Windows users, PuTTY is a great tool for generating and using SSH keys.
- Download PuTTYgen from PuTTY Download.
- Follow this DigitalOcean guide to:
- Generate your key pair.
- Save the public and private keys.
- Upload the public key to your server.
Locking Down Root Password Logins
To enhance security, disable root password logins:
- Edit the SSH configuration file:
nano /etc/ssh/sshd_config- Locate and update the following line:
PermitRootLogin without-password- Restart the SSH service:
sudo service sshd restart